In networking, programmed devices communicate with each other, with or without human interaction, across a building or across the world. Standards set by organizations such as the IEEE (Institute of Electronic & Electrical Engineers) are adhered to by equipment and software manufacturers, providing a reliable platform where devices and software from many vendors can be interconnected together to achieve a specific communications goal.
The proliferation of networking is often compared to our road and highway system in America. If your business location represents a computer, the driveway at your building is the local area network or LAN connection that allows you to readily travel to other locations within your near vicinity. The on-ramp for a multi-lane freeway represents an Internet ISP connection, which provides fast travel between towns or across the country.
The growth of the Interstate highway system radically transformed American life in the last century. Networking is providing the same radical transformation of the electronic security business. Utilizing the millions of available wired and wireless connections already in place, progressive security installation companies are installing network cameras, intercom systems, video servers, access control systems, and other electronic security components. Such installations not only leverage existing cabling and Internet connections, but also provide exciting new services and options that security dealers can provide for their clients. Let’s take a look at the various technologies that make up this exciting new opportunity for security device communications.
The Cable
The cables connecting networks can be viewed as the roads, highways, and driveways that data communications ride upon. Typical copper cable used for networks is usually UTP, or unshielded twisted pair. A UTP cable is most often four twisted pairs of 24-gauge copper, with special jacketing and insulation to reduce the effects of electromagnetic interference (EMI), radio frequency interference (RFI), and crosstalk interference between active pairs underneath the same cable jacket.These cables typically are installed by pulling one or two UTP cables out to each desktop location in a building, with the other ends of each cable being terminated in a telecommunications closet, which may house hundreds of such cable ends. In the telecommunications closet, cables are connected onto the larger local network or LAN, using electronic devices such as hubs, switches, and routers to direct traffic.
Another type of cable commonly used for connections between telecommunications closets is fiber optics, which are glass strands that provide high-speed and high-bandwidth capacity.

The Communications ProtocOL
Ethernet is the most common protocol or computer language used for wired network communications. Like the laws that govern our driving habits, Ethernet is a set of rules that allows for the speedy transmission of data packets from one computer to another.Computers connected to an Ethernet network possess a Media Access Control (MAC) address, which is used by the computer to identify itself to other users on the LAN. Like the Vehicle Identification Number (VIN) on the dashboard of your automobile, unique MAC addresses are placed in the firmware of each network-enabled device at the factory.
The Ethernet protocol fragments data to be transmitted into uniformly sized packets, with each packet including the destination and source computers’ addresses, a sequence code (packet #14 of 143 total packets, for example), the data payload which can be audio, text or video, and the frame check sequence, which provides a sum-check for error correction.
Transmitted packets are collected by the receiving computer, put into proper order, stripped of their now-unneeded addressing information, and sent into the receiving computer’s software for viewing or other purposes.
Today’s typical Ethernet local network operates as a 10/100 system, providing both 10 and 100 megabits per second (Mbps) communications between devices. Although these are the rated data speeds, cabling and connection anomalies generally reduce the actual communications bandwidth of a typical 100 Mbps network to between 50 and 60 Mbps actual throughput.
Wireless Ethernet
Wi-Fi, which stands for wireless fidelity, is the wireless equivalent of Ethernet. Wireless connectivity can be added to any wired Ethernet network by adding a Wi-Fi access point or a combined Wi-Fi/wired Ethernet router. Wi-Fi uses the same addressing scheme as Ethernet, and wired and wireless devices can co-exist on the same LAN, provided that all devices, wired or wireless, each have a unique IP address. Wi-Fi connections will typically provide between 11 and 40 Mbps of data throughput, with the bandwidth decreasing as the distance between devices and/or the signal strength weakens due to interference or other factors.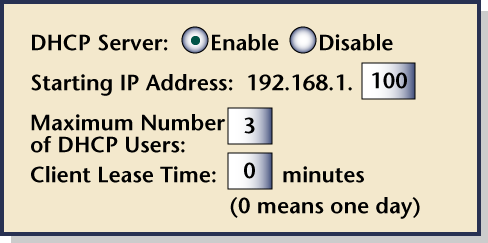
IP Addressing
While automobiles each have a unique VIN, states and countries issue license plates that provide another type of identification and addressing for each vehicle. Networks use Internet Protocol or IP addresses to place individual computers into specific local area networks. IP addresses identify specific computers as members of a particular communication group.While MAC addresses are burned in at the factory and are not normally changeable, IP addresses are readily changed and manipulated by Information Technology (IT) personnel, and increasingly by security technicians installing network-enabled DVRs and other security equipment.
Current IP addresses are in the format of four groups of numbers called octets, separated by periods. A common LAN IP address may look like this:
192.168.2.21
No number set or octet can be of a higher value than 255.
IP addresses also are used for Internet communications.
Within a specific network, every device must have a unique IP address. No two (or more) devices on a LAN can have the same IP address, and no two devices on the Internet can have the same IP address.
Many states offer vanity plates where the user can define what combination of letters and numbers they want. This corresponds to one of the two methods of IP addressing, that being static IP. Static addressing is where a user programs a computer or network device with a specific IP address that typically is rarely, if ever, changed. Static IP addressing is most often used in small networks that experience few additions or changes of devices.
The second method of IP addressing is called Dynamic Host Control Protocol or DHCP. A specific device or computer on the network functions as a DHCP server, and automatically provides IP addresses to network devices when they’re connected. DHCP is the prevalent way that IP addressing is managed in networks both large and small, as the DHCP server keeps track of which network machines have which specific IP addresses at any particular time.
DHCP servers are programmed to issue a specific number of IP addresses, within a settable number range. Here’s an example:
This server will issue three total addresses, ranging from 192.168.1.100 to 192.168.1.102. This provides an element of security, as only three computers can receive a DHCP IP address at any given time. The DHCP address being used by a particular computer can and will change, such as when a computer is turned off and turned back on.
It is important to understand that a LAN can function with both static and DHCP addresses at the same time, as long as there is no duplication of specific IP addresses.
This is of particular importance to the programming of security devices such as network-enabled intercoms and video servers. To connect to a specific intercom station, for example, we need to know its IP address. If the device is receiving a DHCP address, and it changes, what’s the new address? Although the new address can be obtained by interrogating the DHCP server itself, this is not practical. Network security devices such as cameras, DVRs, and intercoms must be issued a static IP address to allow ready access to them, either over the LAN or from the Internet. If a client uses DHCP for their network, the security technician must program the security devices to otherwise unused static IP addresses.
Internet Service Providers (ISPs) generally use DHCP to issue Internet IP addresses to cable modems and DSL adapters. If a client has a DHCP-addressed Internet connection, and remote access to a DVR or network camera is desired, a Dynamic Domain Name Service (DDNS) can be utilized to track the Internet IP address at the client’s location. The alternative is to have the client purchase a static Internet IP address from their ISP, which will cost more and may or may not be available from a particular ISP.
Software Ports
Just as the radio in an automobile has various channels, IP communications uses separate channels, called ports, to establish various two-way connections between devices on a network. There are 65,535 software ports used in IP communications. One commonly used port is port 80, which is the http or HyperText Transport Protocol.Ports are important to understand, as security technicians must select the proper port or ports to be used to communicate with a network-enabled security device. Also, firewalls and routers must be programmed to allow access from outside the local network to specific ports in the LAN to provide Network Address Translation (NAT). These settings will allow a user to connect to a network-enabled security device, such as a DVR, from any Internet-connected computer, provided that the DVR is connected to a LAN which is also on the Internet, and the user has the correct IP address, port number, user name, and password.



