FIELD GUIDE TO MONITORING: Ask the Expert
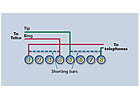
Diagram 1
Getting More from Monitoring
Q: I frequently install burglary, medical alert, critical event, and fire alarm systems connected to my central station, but I am looking to expand my business. What other types of monitored systems can I offer to make more efficient use of my central station?A: There are a number of other systems that lend themselves to remote monitoring. You may currently be installing access control and video as stand-alone systems, but often they are easily adopted for remote monitoring, offering many benefits over non-monitored systems.
In a typical access system you install the readers, controllers, and assorted locking hardware all connected to an on-site head end computer for data entry and reports. Many of these systems also can be installed with a single computer remotely located in your central station, providing the head-end for multiple systems, utilizing a broadband or even POTS line connection to the remote locations. This reduces the cost of the installation because you do not need to purchase a computer for each installation, and it simplifies the user’s life since he or she does not have to maintain the software or database.
The user pays a fee to you for data entry and any reports that he or she needs either on an as-needed basis or as part of a fixed monthly charge. With some access control software it is even possible to provide the user with a Web portal for performing data entry, controlling the system, or running reports from any computer that can connect to the Internet.
Remote video is another avenue to expand your central station offerings, providing alarm verification, video guard tours, e-mail transmission of video images directly to the end user, and user “look-in†to better manage their business. The advent of false alarm fines and dispatching ordinances has spurred the growth of alarm verification; what better way to accomplish that task than to be able to see exactly what caused the alarm?
This is easily accomplished by providing a DVR with some means of remote connection that your operators can use when an alarm signal is received. You also could install remote video systems that will automatically send video images to your central station from the location when an alarm occurs. With either of these systems your operators can view the images in real time, view images that were recorded at the time of the alarm, save the video images to some recordable media, and even e-mail the images to the user or police department.
Video guard tours allow your operators to periodically connect to the remote video system and verify that everything is normal. This can be particularly useful for unmanned locations or areas that are closed, such as hazardous locations, power plants, water treatment plants, waste disposal facilities, or vaults. User look-in allows an authorized individual to remotely connect to the video system and check on the location at will. This can be very useful to a company that has multiple locations and wants to make sure that each location is properly staffed and maintained.
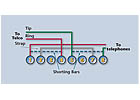
Diagram 2
What Is the Difference between RJ31X and RJ38X Jacks?
Q: I have always used an RJ-31X jack to connect my digital dialer alarm communicators to the telephone line, but a colleague told me that he uses an RJ-38X jack. What is an RJ-38X jack and why does he use it?A: Before I address your specific question, I think a brief explanation of the RJ-31X jack is in order. The jack provides a means of connecting a digital dialer to the telephone network in a manner that allows the communicator to seize the telephone line when it needs to send information to the remote monitoring office. The act of seizing the telephone line electrically disconnects all other telephones at the location so that they cannot interfere with the transmission of data.
In order to accomplish this task the jack must be wired before all other internal telephone wiring. Both jacks have 8 connections and 2 shorting bars. The incoming telephone line is connected to terminals 4 and 5, and terminals 1 and 8 bring the telephone line back out to any other telephones that may be installed at the location. The shorting bars are used to provide continuity to the telephones when the digital dialer’s cord is removed from the jack. While the dialer is plugged in they are open, but if the cord is removed they short terminals 5 to 8 and 1 to 4, maintaining telephone service to all internal telephones.
The difference between an RJ-31X jack and an RJ-38X jack is that the RJ-38X jack also has a jumper installed between terminals 2 and 7. This jumper is used to allow the dialer to monitor the connection of the jack by connecting it to a 24-hour zone of the control. In this way, if the cord is removed the zone will trip, alerting the user of a potential problem. Some control panels are designed to automatically monitor terminals 2 and 7 and if you use them you should install an RJ-38X jack. If the control does not have this capability you can still use the cord supervision feature of an RJ-38X jack, but you will need to program a zone to monitor the cord.
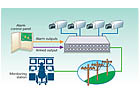
Diagram 3
What’s Involved with Remote Video Monitoring Systems?
Q: I have heard about using video for alarm verification but I am not sure how to install that type of system. What is involved in installing video verification systems?A: With the constant focus on reducing false alarms, various methods of verifying alarms before dispatching is becoming more and more popular and, in fact, sometimes required by local police departments. The verification process may take the form of calling the location, audio listen-in, or video look-in – depending on the equipment installed and capabilities of the remote monitoring office.
There are two basic types of video verification; the first method requires that the monitoring office establish communication with a video system, usually a digital recorder installed at the protected premises. Once communication has been established the operator can manually select which camera or cameras to view for the time that the alarm occurred. Depending on the features of the DVR, the operator may be able to download and save to a disk or similar medium the images that are viewed, or possibly e-mail the images to the police or an authorized party.
The second method employs a device that will automatically contact the monitoring office and transmit images from the camera or cameras that are in the area of the alarm. In order to use this technique the detection devices that are in areas with cameras are connected to the alarm control panel and outputs are assigned for the devices that are then used to activate the video transmitting system. Sometimes a summary alarm output is used to activate the video system, so that any alarm will cause the video system to transmit images to the monitoring station. In order to control the video system, an armed/disarmed output from the alarm control panel is used to turn the video system on and off, preventing it from sending images while the premises is occupied.
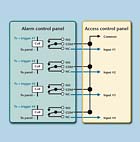
Diagram 4
The diagram (Diagram 3) shows the basic equipment and connections that would be used for a video verification system that employs an automatic video transmitter. If a DVR-based system is used, then all that is necessary is to connect a communication line – either POTS or broadband – to the DVR and provide the monitoring station the information necessary to establish a remote connection to the DVR.
Remote video systems have a number of uses other than for alarm verification. They can be used as video guard tours, allowing the remote monitoring station to periodically check the location; to monitor remote hazardous or unmanned locations; to transmit images of who opened/closed the premises; and to allow management to verify that the locations are properly staffed and operated.

Diagram 5
How to Convert Voltage Outputs to Dry Contact Inputs
Q: I want to connect alarm outputs from the security system to an access control system at the same location. My alarm control only has voltage trigger outputs, but the access system requires dry contact normally closed inputs. How can I convert the voltage triggers to dry normally closed contacts?A: It is often necessary to convert voltage outputs to dry contacts for interconnection of system components or to control voltages/ currents that exceed the available power from the system. Fortunately, there is a very simple, readily available device that can accomplish this task. This device is called a relay.
A relay is an electromechanical device that uses electromagnetism to operate a set of contacts, which can be used for many purposes. Before selecting a relay you must know what the operating or input voltage is, how much current is available, the voltage/current of the switched device, and what type of switching is desired.
The operating voltage is determined by the source of the input, in this case the alarm control panel. The voltage/current of the switched device is the inputs of the access system, which are typically under 24 volts and only a few mA. Relay switching is rated by the number of poles being switched and the number of contacts required. A typical relay contact is SPDT, (single pole double throw). This means that the contact will have 1 common, 1 normally open, and 1 normally closed connection. A DPDT relay, (double pole double throw) will have 2 sets of contacts each with 1 common, 1 normally open, and 1 normally closed connection.
For this application you should check to determine the voltage and current provided by the alarm control panel, such as 12 volt 50 mA. Because all you need is a normally closed contact, a SPDT contact will suffice – actually a SPST (NC) contact will work but I find it is better to have both NO and NC contacts available for increased flexibility.
This diagram (left) shows the connection required to connect relays to convert 4 voltage outputs of the alarm control panel to 4 NC contacts that can be connected to the access control system.

Diagram 6
A Custom Monitoring Scenario
Q: The access control system I have installed has separate relay outputs for abnormal events such as door held and door forced open. I want to connect those outputs to the security system so that these conditions can be remotely monitored, but I only want to use a single zone for both events. How can I combine the two relay outputs into a single zone of the security control?A: Frequently it is desired to combine multiple outputs into a single contact for monitoring or to allow multiple events to activate a single local audible or visual indicator. How the outputs are combined depends upon whether the outputs are normally open or normally closed.
Simply put, normally open outputs are connected in parallel, while contacts that are normally closed are wired in series. Because the terms normally open and normally closed are sometimes misunderstood, we will assume that normally open outputs short when an event occurs and contacts that are normally closed open on an event.
The diagrams (on facing page) show the field connections necessary to connect 2 normally open contacts into a single normally open contact and the field connections necessary to connect 2 normally closed contacts into a single normally closed contact. If more than 2 outputs need to be combined, then you can simply expand the connections to allow an unlimited number of contacts to activate a common trip.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!