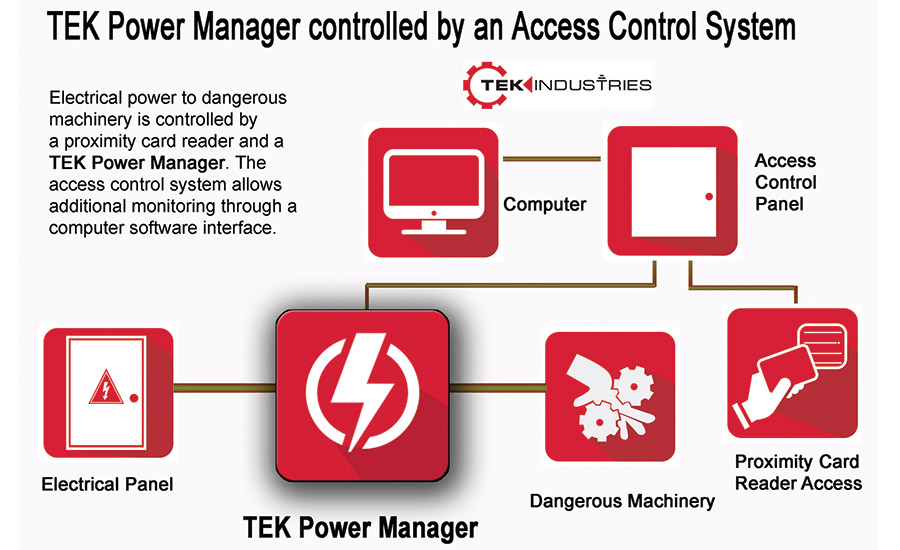
TEK Power Managers from TEK Industries allow systems integrators to manage power for safety, security and productivity applications, adding both services and RMR potential. The UL-listed devices — models TV-1.5 and TV-1.5L — integrate with existing alarm, access control and building management or process control systems and solutions.
With higher voltage components shielded to allow unrestricted access to low-voltage components by security technicians, TEK Power Managers can be easily incorporated into new and existing low-voltage and higher-voltage infrastructure. By combining Power Managers with traditional environmental or security systems and/or sensors, integrators and end users can effectively control and monitor high-voltage circuits to create more efficient environments for a wide range of commercial and residential customers.
“These products are designed to solve challenges for the integrator,” said John Kuiken, national product manager for TEK Industries, Vernon, Conn. “Low voltage can now control high voltage. We originally created this for manufacturing environments where you have high-voltage dangerous equipment and they wanted to be able to control the power. After we made them it became apparent that the greatest value of these is for energy savings. Now you can use the access control system to schedule power to a high-voltage system, making it so someone can’t use the equipment unless they swipe a card.”
TEK Power Managers can be used to improve safety around dangerous machinery, increase operator productivity, or reduce electric energy consumption, for example. The Power Managers can be managed remotely via the Internet or wireless connections, allowing for managed alarm and access control services, and also reducing truck rolls and onsite customer visits. By connecting Power Managers to an alarm, access control or building management system, usage data can be recorded and monitored. Systems can also be programmed to send an email notification or text alert with information regarding status, events or usage.
Once the box is installed by a high-voltage contractor, an easy switch makes it a low-voltage device on the network, just like a motion sensor or a camera, Kuiken explained.
“Normally integrators don’t touch high-voltage equipment,” he said. “This is an entry into that world and it is something they are often asked to do, but it is usually a dead end, or involves an ongoing relationship with a high-voltage contractor. Now they have the opportunity to manage higher voltage circuits, or even go back to any system they have already installed and add this feature. Any access control system can now control high-voltage equipment.”
TEK Boxes can be controlled by almost any low-voltage switch, contact or sensor. The list of devices includes key switches, numeric keypads, timers, security and environmental sensors, video cameras, and any alarm or access control system. These combinations allow integrators to:
• provide power only for individuals who present a valid key, code, proximity card, or biometrics;
• provide equipment power only when a manager is present;
• supply equipment power on a schedule;
• log all usage events and receiving alerts or alarms on any undesired activity;
• deny or provide power remotely;
• shut down power when an unauthorized person gets too close to a machine or process;
• shut off power during periods designated for reduced power consumption;
• cut power during extreme events to ensure safety and prevent equipment damage.
The TB1.5 is the workhorse model in the Power Manager Line. This larger (14-in. by 12-in. by 4-in.) enclosure has a low-voltage partition suitable for holding a variety of other vendor control and relay boards. At 10 in. by 8 in. by 4 in., the TB-1 is a machine-mountable version. It has all of the features of the TB-1.5, without the extra room in the enclosure for other vendor control and relay boards.
“They are made to be customized to the integrator’s system,” Kuiken said. “Traditionally the integrators haven’t had a good relationship with building management systems. This is a way for the security integrator to retain customers and to get business back.” Visit www.tekind.com for more information. —