ACCESS CONTROL & IDENTIFICATION
Trends in Access Control Software
Software and the cloud have made access control more powerful, versatile and affordable than ever.
![Screenshot_Security-Score_SC5.8-Dashboard_2736x1824_3x2[1]](https://www.sdmmag.com/ext/resources/Issues/2020/April/Screenshot_Security-Score_SC58-Dashboard_2736x1824_3x21.jpg?t=1586793661&width=1080)
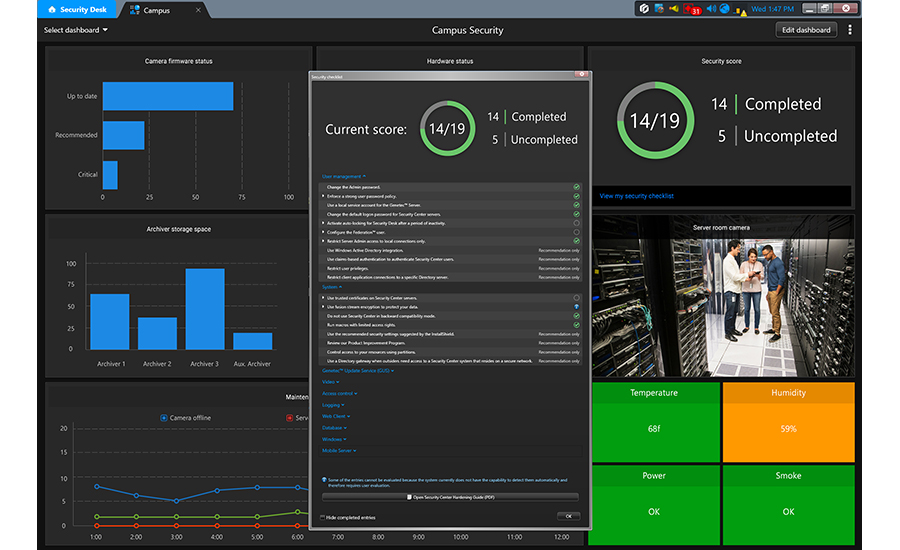
The Genetec Security Center platform includes a Security Score widget that displays a system’s compliance with cyber security hardening best practices in real time so users can assess their cyber security exposure and address any potential issues.
IMAGE COURTESY OF GENETEC

ACT365 cloud-based access control and video management from Vanderbilt Industries allows security leaders and business owners to manage their devices from a centralized platform, either on a PC or with a mobile device.
IMAGE COURTESY OF VANDERBILT INDUSTRIES
![Screenshot_Security-Score_SC5.8-Dashboard_2736x1824_3x2[1]](https://www.sdmmag.com/ext/resources/Issues/2020/April/Screenshot_Security-Score_SC58-Dashboard_2736x1824_3x21.jpg?t=1586793661&width=150)

More customers are using access control, and doing more with it, than ever before — and the industry has advances in access control software to thank for that. Functions that previously were hardware-based now may be provided through cloud-based software, making access control more affordable; and application programming interfaces (APIs) enable access control software to be integrated with other systems such as video or enterprise requirements planning (ERP), making access control more powerful and versatile.
SDM talked with companies that develop access control software and with security integrators that sell access control about seven key trends in access control software.
1 The Cloud Comes on Strong
Cloud-based access control is coming on strong.
Mark Hillenburg, vice president of marketing for Springfield, Mo.-based access control technology provider DMP, notes that half of the 5,000 doors of access control that the company sells each month go into cloud-based management software.
Rence Coassin, owner and president of American Total Protection, a security integrator based in Hamden, Conn., and Melbourne, Fla., notes that, “Access control is a product that everyone wants — they just need to decide if they want to pay for it.”
Because cloud-based options require minimal upfront investment, that makes the decision easier, Hillenburg says. “Some people are buying access control now who wouldn’t have before the cloud,” he says.
The move to the cloud benefits integrators as well by providing a source of recurring monthly revenue that wasn’t traditionally associated with access control in the past, Coassin notes.
“Our business is an RMR model,” says Chris Burton, operational support manager for Nashville-based security integrator ADS Security, adding that the rise of DIY security is having an impact. “On the residential side, we’re losing RMR and we have to make it up somewhere.”
Before cloud-based access control, ADS offered hosted access control, which enabled multiple users to share access control software running on ADS’s servers, which helped minimize the customer’s investment, but had one key drawback. “You couldn’t give access to the customer [to system controls],” Burton says. Instead, the customer had to contact ADS when changes to the system were required.
The cloud-based DMP offering that ADS uses gives end customers the ability to make system changes themselves via a remote interface.
Another benefit of cloud-based access control software: “We hardly ever lose cloud access control customers,” Burton says.
2 Enterprise Customers Embrace the Cloud
Initially the typical user of cloud-based access control was a small to medium-size business, as these companies are least likely have staff to manage and maintain the software. More recently, even larger enterprises that have their own tech staff are looking to move access control to the cloud. These companies may have begun by moving other types of software to the cloud and now have enough confidence in the cloud approach to move access control there, as well.
“The biggest benefits for enterprises are anywhere, anytime access and less overhead,” says Marcus Logan, global offering leader for enterprise solutions for Atlanta-based Honeywell Commercial Security. “And [the need] to manage physical or virtual servers goes away. It converts access control from a capital expenditure to an operational cost.”
Some enterprises like the cloud approach but operate their own private clouds, however. Accordingly, some access control suppliers support both private and public cloud options.
3 Intelligence Moves to the Edge
Traditionally, access control software resided on a centralized controller, but as the cloud catches on, another trend is for intelligence to move toward the edge of the system. Several sources interviewed for this story see intelligence moving to the readers.
Milwaukee-based supplier Johnson Controls has developed access control readers that provide some of the functionality of the traditional access control panel and that communicate directly with cloud-based access control software, eliminating the need to connect them to a premises-based controller via a local area network. The reader is powered locally, and end users have an app on their smartphone that serves as a credential to communicate with the reader. Decisions about whether to allow a person entry are made by the reader in communication with the cloud.
“The reader is the door controller and doesn’t need to be outside the door,” explains George Martinez, director of product management for cloud solutions in the Global Security Products unit of Johnson Controls. “You don’t need the LAN so there is less attack surface.”
At press time Johnson Controls planned to launch the product in March.
Eric Green, chief product owner for enterprise solutions for Honeywell Commercial Security, also notes a trend toward greater intelligence at the edge and, like Martinez, expects to see more intelligence and decision-making pushed out to the readers.
Key Cloud-Based Access Control Terminology
Hybrid cloud: Cloud-based access control that is backed up by premises-based functionality in the event that a company’s connection to the cloud is interrupted or communication with the cloud is not possible for another reason.
Private cloud: Cloud-based access control in which the access control software runs on remote servers or virtual servers operated by the client company.
Public cloud: Cloud-based access control, typically provided by the supplier of the access control equipment and delivered from servers or virtual servers operated by the supplier.
Software-as-a-Service (SaaS): A public cloud approach to access control in which the supplier typically charges customers a monthly service fee on a per-door basis.
4 Integration Gains Momentum
Using software to integrate access control with other systems is another increasingly popular request from business customers. In some cases, an access control supplier may make an agreement with a supplier of video surveillance so that the two systems can work together. Alternatively, some access control suppliers offer application program interfaces (APIs) for their software to enable customers or other developers to create integrations of their own.
A popular integration for customers of Parsippany, N.J.- based supplier Vanderbilt Industries is one that links access control software with enterprise requirements planning (ERP) software, notes Eric Widlitz, vice president of North America Sales for Vanderbilt Industries. This enables employee data from the ERP system to flow through to the access control system so that if, for example, an employee quits, the company only has to indicate that in the ERP system and the access control software will be automatically updated as well, eliminating the need to rekey the information to prevent the ex-employee from gaining access to the workplace.
Business customers also may require system integration in order to have a single credential that serves multiple purposes, observes Jonathan Moore, director of product management for Torrance, Calif.-based supplier AMAG Technology.
“They want a secure credential for access control but will say, ‘It better work with the printer,’” Moore comments.
Some businesses, particularly those that acquired other companies, may have access control from different manufacturers at different locations and may want them to function as a single system. To address this, “We’re starting to see the rise of industry organizations like PLAI,” Moore notes. PLAI, which stands for the Physical Logical Access Interoperability Initiative, is an open standard designed to enable access control from disparate manufacturers to be integrated to function as a single system.
5 Another Source of RMR
Moving access control software to the cloud isn’t the only way that access control can generate recurring revenue. Some suppliers are offering other software-based services that business customers pay for as a service, although billing may be annual, rather than monthly.
For example, the VI Connect service from Vanderbilt Industries is designed to monitor all components of an access control system that has been integrated with a third-party system to help ensure functionality. School districts were the early adopters of this offering but as Widlitz notes, the offering is now being adopted by other organizations, as well.
6 Regulations Drive Access Control Requirements
Regulations also are driving access control software requirements, says Despina Stamatelos, product marketing manager for access control for Montreal-based Genetec. Government agencies increasingly are looking for systems that are compliant with Federal Identity, Credential, and Access Management (FICAM) requirements, which impacts software and other elements of the system, Stamatelos says.
She adds that electric companies increasingly are looking for access control to meet the requirements of the North American Electric Reliability Corporation (NERC), which also impacts access control software.
Even regulations established by the European Union (EU) can affect access control software.
Logan and Green note, for example, that California and other states are adopting or looking to adopt rules similar to the EU’s General Data Protection Regulation (GDPR). Those rules prevent companies from storing employees’ names on servers outside company locations. That means that companies using cloud-based access control would have to store employee data by numbers, rather than names, when housed in the cloud. Such rules also may apply to companies that have European citizens working in the U.S., the Honeywell representatives note.
The Physical Logical Access Interoperability Initiative
The Physical Logical Access Interoperability Initiative (PLAI) was established by the Physical Security Interoperability Alliance (PSIA) with the goal of enabling access control software from different manufacturers to interoperate.
PLAI is designed to:
- provide instantaneous invoking and revoking of security privileges across disparate physical access control systems;
- provide support for logical privileges and physical access in multiple business locations and campuses;
- provide support for temporary access credentials when employees travel to remote sites and sync security access with different physical locations;
- minimize risk because all logical and physical access privileges are based on a single authoritative source (for example, it is impossible for a PLAI-compliant physical access control system to contain two versions of an active employee’s name because it is drawing the employee identities from the authoritative IT/HR source).
Additional information is available at https://psialliance.org/all-about-plai/.
7 Facial Recognition Coming Soon
Facial recognition software, used in combination with integrated video surveillance, will be coming to access control soon.
Honeywell is working on what Logan calls “frictionless” access control that will use facial recognition to allow authorized parties to enter a facility, eliminating or reducing the need for a credential. The company has used access control software supporting that capability at several corporate beta sites and expects to have an offering commercially available within six months, according to Logan.
Clearly there has been a lot of innovation in the access control software area and that innovation shows no signs of fading any time soon.
More Online
For more information about access control software, visit SDM’s website where you will find the following articles:
“The Cloud is a Win-Win for Security Integrators and End Users”
www.SDMmag.com/cloud-is-win-win-integrators-end-users
“The State of the Access Control Market in 2019”
www.SDMmag.com/state-of-the-market-access-control-2019
“The Unified Approach”
www.SDMmag.com/unified-approach
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!