Home » cloud security
Articles Tagged with ''cloud security''
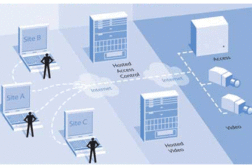
The Cloud: Secure Enough for Security
We can only secure our assets if we’ve first secured our technology.
July 18, 2011
Be in the forefront of security intelligence when you receive SDM.
Join over 10,000+ professionals when you subscribe today.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing